0081
Andrew Smith*
Department of Communication and Systems, The Open University, Milton Keynes, UK
Abstract
This paper describes the early stages of research and development of an educational environment designed to enable learners to participate in remote, group based large-scale activities based on local area network and wide area network technologies working on a range of systems and within different learning situations, such as in class group work, remote group work or independent learning. The environment covers specifically routing, switching and wireless principles in the domain of computer networking. This is accomplished using the ‘multiuser functionality’ feature found within the Cisco Academy programme, Packet Tracer application. The initial research explores how a ‘virtual Internet’ can be implemented to enable learners to engage with the scale and complexity of the Internet without interacting with active routing infrastructures thereby interfering with others. Different communities of interest from Cisco Systems as well as their Academy Programme academic affiliates have contributed to the development of the resource as well as to research into how individuals participate in learning as a result of using this software. This paper tells the story of the iterative action research process with two initial learning situations of ‘remote many’ participation and ‘in class many’ participation in a large scale networking exercise. As research is still in the development process, this paper explores the experiences and observations gathered from engaging with the two learning scenarios, describing how each interaction exercise was perceived by participants and their educators. Initial findings from both activities indicate that the concept of an ‘Internet on the Internet’ to deliver simulated practical learning has considerable potential and brings an alternative dimension to the practical learning experience. Research is ongoing, with the work in this paper informing the continual iterative process.
Keywords: constructivism; situated-learning; simulation; Packet-Tracer; collaborative-learning
*Corresponding author. Email: a.smith@open.ac.uk
(Received 27 February 2011; final version received 22 June 2011; Published: 31 August 2011)
ISBN 978-91-977071-4-5 (print), 978-91-977071-5-2 (online)
2011 Association for Learning Technology. © A. Smith. This is an Open Access article distributed under the terms of the Creative Commons Attribution-NonCommercial-NoDerivs 2.0 UK: England & Wales licence (http://creativecommons.org/licenses/by-nc-nd/2.0/uk/) permitting all non-commercial use, distribution, and reproduction in any medium, provided the original work is properly cited.
DOI: 10.3402/rlt.v19s1/7777
The Open University in the UK commenced offering the Cisco Academy Programme, the Cisco Certified Networking Associate (CCNA) in 2005 as a blended distance-learning course as part of the Foundation Degree in Information and Communications Technology (ICT). Since inception this course has reached in excess of 4000 students across the UK and some internationally, all taking the course in a blended distance-learning mode.
A challenge is managing access to course specific router and switch technology, giving students an essential opportunity to engage in interactive practical activities. This enables each student to acquire a view of the complexity involved in network environments, such as a corporate wide area network infrastructure or the Internet itself.
The course team responsible for the management of delivery explored a range of tools, including Netlab+ distributed by Netdev Group http://www.netdevgroup.com and Packet Tracer from Cisco Systems Inc. (Academy site at http://www.cisco.com/web/learning/netacad/index.html This included setting a range of assessment tasks using these tools and experimenting in group based delivery as researched by Smith and Moss (2008) and Prieto-Blázquez (2008), The research focused on the setting of course assessment items and the management of synchronous and asynchronous learning using both resources.
With the introduction of multiuser functionality in Packet Tracer version 5.0 and the publication of the Packet Tracer Multiuser Protocol (PTMP) (Wang 2008), the Packet Tracer application enables students in disparate locations to interact on a common simulated practical activity.
As a network simulation environment, Packet Tracer provides simulated router, switch, server, workstation and networking protocol resources for students and educators to create diverse and complex networking scenarios, extending the pedagogical and practical experience during participation in the Cisco Academy Programme.
The Cisco Certified Networking Associate (CCNA) version 4.x exploration and discovery curriculum contains embedded laboratory exercises for the students to complete. These are in-class on live networking technology, remotely via the Netlab+ system or by launching the Packet Tracer application from within the curriculum content. Packet Tracer activities are goal based, giving students attainable milestones and feedback by indicating the completion percentage based on the given activity scenario.
As a simulation tool, the ‘operating system’ deployed on simulated workstations and routers forms a critical subset of the actual technology, presenting similar behaviour, performance and idiosyncrasies within a contained experience.
The inbuilt multiuser functionality allows students and academic centres to create environments that can interact, irrespective of locale, type of academic institution and supporting network infrastructure. This results in the ability for two students, in any location, being able to create a connection and complete a practical activity of their choice. Figure 1 illustrates two independent instances of packet tracer using a peered network connection, with two simulated workstations exchanging simulated network traffic.
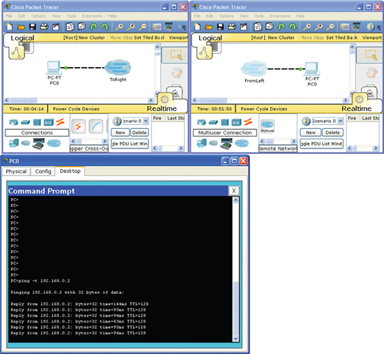
Figure 1.
A peered example of Packet Tracer Multiuser communication.
A multiuser connection can be established on any Transmission Control Protocol (TCP) port, with ports 38,000–38,999 selected by default. An academic centre may elect to use an alternative port according to local networking security policies.
Packet Tracer is therefore able to handle multiple multiuser connections between many of users. It can support one:one, one:many and many:many options, with either remote or local collaboration scenarios available to students and academic centres alike.
Designed to be ‘easy to use’ anyone using the Packet Tracer application can quickly create a multiuser connection by using the default port and an Internet Protocol (IP) Address or established domain name as illustrated in Figure 2.
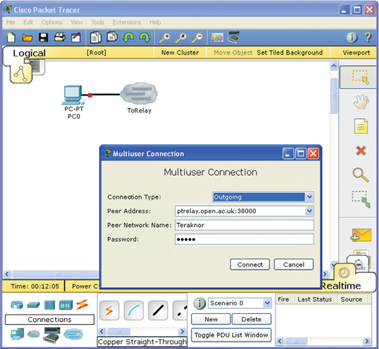
Figure 2.
Creating a multiuser connection from Packet Tracer.
With the many:many multiuser interconnection available, multiple academic centres may create a mesh of connections, with students interconnecting to a collaborative environment internally or externally to complete a range of practice-based learning activities.
There is a clear pedagogical benefit in allowing students and academic centres to connect across a Local Area Network (LAN), a Wide Area Network (WAN) or the Internet via Packet Tracer for their work. However, the application presents a serious networking trust issue in the explicit exchange of an IP address or domain information by any participant.
Any one:one connection between peers would carry an implied personal trust, assuming that both parties are aware of the other's need to connect. With each party present at the workstation hosting the packet tracer application, they are able to permit or deny any initiated connection. Packet Tracer at this level does not allow anonymous connects unless the user specifically configures the application to do otherwise; this is not a default state.
With a one:many, in an internal scenario, the same trust principle as the one:one connection relationship is implied. The academic leading the practice-based session will be present to invoke the activity and therefore trust any incoming connections.
At the stage where centre-to-centre communication takes place and communication has to interact with an academic organisation's network security policies and firewalls, a question is raised regarding the authenticity of the remote connection and the trust surrounding from whom the connection may be coming. The complexity of the question increases with each new connection and potential participant.
Furthermore, when a remote learning scenario occurs, normally with students who study via blended distance-learning, the likelihood is that students have never met and therefore have not formed an albeit basic trust relationship. There is a need for social exchange to engender trust (Xueming 2002), and this raises an immediate issue, insomuch as students are now expected to exchange their IP address, port or domain information to enable direct communication with someone with whom they have no personal contact or no potential conscience when it comes to unethical behaviour. With the lack of formal hierarchy, Gurzick et al. (2011) identify that there need to be leaders and designated participants in an online collaborative environment.
Therefore in the establishment and creation of any one:one connection between distance based students (in respect of Figure 2 who may have never met and therefore have a lower trust exchange there is the potential for abuse, via hacking, exploit, denial of service or cyber stalking. This would present many academic centres with the risk of multiple liabilities and thus encourage any reasonable academic or network manager to refuse to allow the multiuser feature to run on their system.
Resolution of this security threat is essential in maintaining trust between distance based students and remote centres. In exploring potential solutions, research focused on the many:many property of Packet Tracer, with the question: “What if a trusted intermediary was available?”
With a many:many scenario, trusted secure devices could be created for academic centres as well as students to interconnect. Now the trust is with the intermediary, as the domain and the port of the intermediary is known to everyone. No individual or academic entity would exchange any sensitive information regarding IP address, domain or TCP port. Therefore creating a relay server, hosting a trusted instance of Packet Tracer, overcomes many of the immediate security and trust issues.
With this in mind, all of the relays could be interconnected in a mesh (Internet like) structure. Having each relay connected to other relays would create a secure physical structure that would support a scalable community of practice, as new relays can easily be added as the community grows. Overarching technical benefits would be:
Secure communication using the PTMP (Wang 2008).
The opportunity to implement a range of technical platforms for each relay implementation, assuring system agnosticism (no single preferred manufacturer or software vendor).
Ensuring that the simulated network infrastructure is adaptable and diverse, presenting no restriction in the learning scenarios being developed by participants.
Resilience, with multiple relays (some possibly acting as intermediaries), overcoming the indiscretions of technology.
Each has differing benefits, in learning delivery and technical deployment, and can be adapted to reflect of local academic and technical need. Scenarios can be designed to encourage practice-based development and situated learning as described by Lave and Wenger (1991).
Students and academic centres have the freedom to create their own local networks on Packet Tracer and interact with the intermediary servers as they wish. In an experimental context, a default file has been provided to ensure everyone has a common entry point into the multiuser environment, giving a constructivist scaffold for a common level of entry, (Rüschoff and Ritter 2001).
In addition, support has been given to the research by the Cisco Systems Packet Tracer development team in developing an add-in; the multiuser connection manager (MUCM) tool manages redundant connections that have remained unused for a predetermined time period so that the system does not become overloaded with them.
Relying on one intermediary relay server limits the potential value in scale and reach of the collaborative opportunity available. The sole purpose of Packet Tracer is to engender understanding of complex network topologies and the interaction of protocols and devices in this environment. The multiuser feature, supported by the formation of a collaborative interlinked mesh of intermediary relay servers, means that the system gains resilience and localisation, with the potential for a worldwide ‘ring’ of systems all interconnecting each accommodating geographic locale specific preferences and academic requirement.
The practical outcome of such a mesh is the immediate advantage is to offer academic centres and individual learners a system able to provide them with the learning experience of building a complex internet work without the political and security complexities of using the ‘real’ Internet.
Packet Tracer provides access to otherwise inaccessible IPv4 and IPv6 address ranges, as well as an extensive range of networking technologies including: DHCP, NAT, STP, VPN, QoS, BGP, OSPF, EIGRP, RIP, dot1q, VTP, in an environment allowing students to make mistakes and learn from their experiences without impacting others.
In a collaborative distance based framework, the creation of an intermediary relay supported a mesh of relay servers. Laurillard (2002) identified how academic centres as well as students can engage in distance based synchronous and asynchronous learning. The use of Packet Tracer in this context exemplifies these findings and allows local technological needs and conceptual needs of the students to be respected at the time of interaction. In addition, the flexible nature of Packet Tracer means that, with suitable core topology design, one group of learners can interact with the system at the same time independent of other learning collaborations. Thus the distance based asynchronous and synchronous, collaboration can co-exist between classes of students in a specific geographic locale as well as internationally.
Assessment based learning may take place using the local Packet Tracer client in the activity mode, with students interacting in a ‘staged’ learning and problem solving scenario thereby providing discovery based exploratory learning.
Having a constructivist ethos, the concept of an environment open to personal interpretation of the student as well as the guiding academic is synonymous with many of the principles proposed by Piaget (1978). The distributed learning methodology supported by Packet Tracer with the multiple sources of information, each giving form in a constructivist paradigm, gives credence to the emergent concept of connectivisim from Landauer and Dumais (1997).
The research programme commenced in September 2009 with distance-learning students participating from the UK Open University's T216 (Cisco Networking/CCNA) and T824 (Advanced Networking/CCNP-BSCI) courses.
The test scenario was for each participant to connect to the relay server via two clients (both on the same local host), create an Extended Interior Gateway Routing Protocol EIGRP peering by:
adding a new local network into the autonomous system routing process for each client instance,
adding at least one workstation for each local network,
pinging the default gateway from each workstation and
pinging each other.
Testing was confined to a one-hour window from 19:00 to 20:00 GMT. During this time over 40 participants joined with a peak of 15–20 different peers in the 19:20 to 19:40 window. To ensure a baseline network behaviour, one host ran a continuous simulated client-to-client ping and a continuous simulated ping to the intermediary server.
The MUCM, managed to rollback connections, ensuring deletion when disconnection notice expired after five minutes.
At 19:40 (estimated) the Packet Tracer application crashed during a period of apparent peak activity. The research team subsequently revisited the test case by examining four scenarios in a controlled test environment:
Emulating the same event, increasing load, to observe the factors leading to failure.
Testing the system on Linux without MUCM interactivity.
Testing the system with MUCM in Windows
Testing the system without MUCM in Windows.
In addition, with all of the scenarios, upon failure the test was repeated without EIGRP present. Early findings have concluded that the 15 second hello timer for EIGRP works within a LAN based multiuser setting but as soon as Internet communication is in play, the application, operating system and transmission latency all combine so that the next hello packet arrives too late for the simulator. This leads to a hold down state and increased application activity.
An additional unanticipated challenge was the need to mentor/coach some of the participants during the session (via skype and email). Anecdotally it would seem that for some, there was a difficulty in understanding the concept of how they were connecting to others in this remote environment.
The first test case proved the potential for disparate individuals from diverse locations to connect and engage in a semi-synchronous, primarily asynchronous practical activity. Following the simple practical scenario, each participant completed the tasks set. Therefore the development of group based participatory activities in the sphere of situated learning of Lave and Wenger (1991) in an online environment.
A key finding, was the recognition that some of the participants needed to understand how to engage with the distance learning scenario. The challenge for the host was enabling the participating group to construct the mind-set to understand how they were each able to participate in this en masse exercise. To understand this, the researchers need to work with groups of students face-to-face to understand where the misunderstanding lay, through either experience or perception of the conceptual network structures. This is a constructivist model (Piaget 1978) as students have to become active participants in the learning process, needing an initial environmental anchor to base their constructed ideas upon.
A challenge in any activity requiring volunteers is the recruitment of those volunteers. Since the initial research there have been three successful interactive scenarios. The timing of these has been principally driven by availability. It was recognised that all participating students need to have a minimum of the Cisco Academy exploration or discovery first course behind them to comprehend the networking terminology and technology.
To avoid other effects, the student age range was kept in a small window, with participating students being either second years on a high school equivalent technical vocational programme or first years on an undergraduate honours degree programme. This gave a range of 17–20 years of age with the majority in the 18/19 year-old age group.
Research sessions were in May, November and December 2010, reflecting academic calendars of each group and availability. The May and November sessions were with two groups of 18 and 11, 17–19 year olds at a college of Further Education. The December session was with a group of 30, 18-20 year-old year one undergraduate students at a London University. Group selection was based on the class/group available at the time suited to the demands of timetable, and availability of the willing volunteer teacher and the researcher.
Each of the sessions was scheduled for a three hour half day block. The first was a morning session 09:00 to 12:30 with break, the second session was 10:30 to 15:00 with intervening lunch break and the third session was a PM session from 14:00 to 17:00 with a short break.
Each session used the majority of the time, with an average of thirty minutes remaining to enable the students to complete an optional challenge activity. In each session the researcher acted as teacher/facilitator whilst the normal session teacher/instructor acted as class-room support and secondary observer.
Each session was facilitated as an in-class teaching session, where each of the student participants was aware that they were helping to test the multiuser functionality of Packet Tracer and get in return additional networking skills (via practice-based learning).
The use of a data projector connected to the teacher's computer running the relay instance of Packet Tracer, provided the students with an essential conceptual cue for students supporting the work discussed by Janitor and Kniewald (2010) . It enabled them to see how their own simulated LAN and WAN was behaving in relation to the greater relay based WAN infrastructure.
Typical of many academic classrooms, each computer running during each session had the same hardware specification and operating system installation, including local policy constraints and user rights. This ensured that each student participating had the same technological advantages/disadvantages as all others during the lifecycle of each activity. The activity was managed in a systematic follow-the-leader step-by-step format, keeping all students at same position in the process.
The group-based activity is presented to students in two parts. The outcomes of the previous research showed that some did not understand the conceptual network and needed a scaffold to base their conceptual viewpoint upon. The student group would commence the activity with a formative warm-up exercise (the scaffold). In this, students were paired and given the task of creating a simple network of two hosts and being able to send a ‘virtual’ ping from one Packet Tracer instance to the other across the academic network as illustrated in Figure 3.
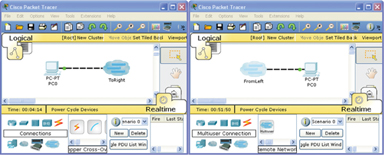
Figure 3.
Peered example of Packet Tracer Multiuser communication.
This short exercise sets the scene and ensures all participants are working from the same stand-point in their ability to use the software. All participants are already low-level users of Packet Tracer, by virtue of their membership as students of the Cisco Academy programme. By introducing the participants to the ‘multiuser’ tool, their understanding of the additional tools available in Packet Tracer is increased.
Following the formative scaffold activity, the students participate in the large-scale activity to build a simulated WAN, with multiple individual simulated LAN's.
The structure of the activity is a replication of the experimentation explored in the first stage of the research, with the relay no longer a remote server, but the teacher's computer. This assists the learning process experienced by the students and observing instructor, discussed by Laurillard (2002). In each session, the teacher's computer is attached to a classroom data projector. Each student is able to see their own multiuser connection locally as well as their remote connection on the teachers Packet Tracer instance thus reinforcing the assurance that they are correctly participating in the practical task and successfully building a remote (otherwise unseen) connection.
The relay instance of Packet Tracer contains a simulated router with a series of simulated switches all connected to a core switch (Figure 4). The simulated protocol selected is again EIGRP and each student is presented with unique IP addresses to use during the exercise.
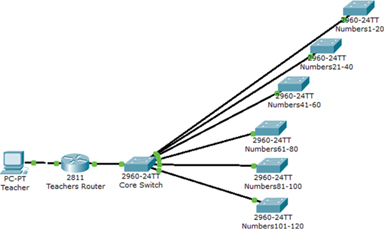
Figure 4.
Teacher relay-server structure.
Routing protocols, as with many network technologies, can be configured in many different ways to achieve the same goal. To remove any confounding variance, all students are presented with an instruction sheet containing the commands they must use. The students own instance of packet tracer is a self-constructed system when assembled, and resembles the illustration in Figure 5. The system is kept simple to reduce potential variance, by ensuring the students have specific devices and cable types to implement.
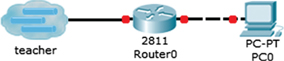
Figure 5.
Student Packet Tracer instance.
Qualitative feedback was collected from each cohort, the intention was to understand their personal viewpoint of their experience in participating in the sessions as well as in the activities.
At the end of each session, before departure, the students were asked to complete a short anonymous questionnaire, with questions listed in Table 1.
|
The questionnaire results are summarised in Table 2. As the groups are small, and the questionnaire short, there are no missing responses; no additional personal information was requested.
From the results in (Table 2), the dominant feedback implies that the students believed that using the simulated practical was a personal benefit, where the responses to questions one and three indicate a high percentage (Table 3) of positive responses to the enquiry about their learning.
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||
It is notable that for the November cohort, the groups of students were in the early stages of their learning for the academic year, whereas the May and December cohorts were either at the end of their respective academic year or semester.
Questions two and four explored the student's experience of Packet Tracer. Apart from two outliers (reason unknown), question two indicated that the majority had not used the multiuser tool beforehand. With Question four, the response indicates an interest held by the students to continue using the multiuser tool in packet tracer. This may have been stimulated by their feelings regarding the preceding session.
In engaging with the practical activities, the students could be seen to personally link constructivist personal concepts as described by Piaget (1978) and readily connect their own private concepts to a visual, simulated physical network environment. This is supported by parallel research described by Lo (2010), who states that “appropriately used collaborative learning activities do promote student learning and student satisfaction”. This is also supported by Hare and Graber (2007) in their research into how students engage in a constructivist-learning paradigm adopting and dismissing misconceptions when playing ‘invasion games’.
The activities have demonstrated that once the student has been given an introduction to the multiuser tool, they are able to engage in a structured activity to build a complex simulated network environment, reflecting the model of situated learning discussed by Lave and Wenger (1991).
Formal questionnaire feedback as well as the in class anecdotal experience of the researcher, reflects an enthusiasm from the learners to continue studies using the Packet Tracer application in this mode.
Research discussed in this paper, allied with prior research suggests that the structured development of a system to create a simulated Internet provides an alternate learning methodology for in-class as well as remote distance-based learners.
The centres involved are willing to host future sessions, inviting the researcher back to continue the same exercise, as well as new different scenarios with their students. Other centres are interested in participating in the research and are willing to engage in the activities described in this paper, as well as working towards more complex scenarios. The challenge for these centres, as for the original participants, is finding the right group at the right time in their year as well as in the study week.
Once the students and teacher/instructors become familiar with the technology and the constructivist learning experience, the plan is to move the activity to a remote ‘central’ relay server model, with more than one centre participating during the research and working on a collective multi-site learning activity.
The author would like to thank Dennis Frezzo of Cisco Systems and his team for inspiration, insight and support as well as the enthusiastic support from Cisco Instructors. Special thanks is due to Paul Wallin of Kingston University (UK) and Ken Lamb, Milton Keynes College (UK) as well as the enthusiastic academy students alas too numerous to mention.
Gurzick, D. et al. 2011. Designing the future of collaborative workplace systems: lessons learned from a comparison with alternate reality games. Proceedings of the 2011 iConference, 8–11 February 2011, Seattle, Washington State, USA.
Hare, M., and K. Graber. 2007. Investigating knowledge acquisition and developing misconceptions of high school students enrolled in an invasion games unit. High School Journal 90, no. 4: 1–14.
Janitor, J., and K. Kniewald. 2010. Visual learning tools for teaching/learning computer networks. ICNS'10 Proceedings of the 2010 6th International Conference on Networking and Services, Cancun, Mexico.
Landauer, T.K., and S.T. Dumais. 1997. A solution to Plato's problem: The Latent semantic analysis theory of acquisition, induction and representation of knowledge, from http://lsa.colorado.edu/papers/plato/plato.annote.html (accessed February 21, 2011).
Laurillard, D. 2002. Rethinking University Teaching: a framework for the effective use of educational technology, 2nd ed. London: Routledge Falmer; 154.Lave, J., and Wenger, E. 1991. Situated learning: Legitimate peripheral participation. Cambridge: Cambridge University Press, 91.
Lo, C.C. 2010. Student learning and student satisfaction in an interactive classroom. The Journal of General Education 59, no. 4: 238–63.
Piaget, J. 1978. Success and understanding. London: Routledge & Kegan.Prieto-Blázquez, J. 2008. An integrated structure for a virtual networking laboratory. IEEE transactions on Industrial Electronics, 55, no. 6: 2334–42.
Rüschoff, B., and M. Ritter. 2001. Technology-enhanced language learning: construction of knowledge and template-based learning in the foreign language classroom. Computer Assisted Language Learning 14: 219–32.
Smith, A., and N. Moss. 2008. Cisco networking: using Skype and Netlab+ for distance practical learning. IADIS e-Learning 2008 conference, July 22–25, in Amsterdam, Netherlands.
Wang, M. 2008. Packet Tracer 5.0, Packet Tracer Messaging Protocol (PTMP), Specifications Document: Cisco Systems.
Xueming, L. 2002. Trust production and privacy concerns on the Internet, A framework based on relationship marketing and social exchange theory. Industrial Marketing Management 31: 111–118.